Ironman Software Forums
Continue the conversion on the Ironman Software forums. Chat with over 1000 users about PowerShell, PowerShell Universal, and PowerShell Pro Tools.

 Discuss this Article
Discuss this ArticleIn this post, we’ll look at how to configure PowerShell Protect to send script execution information to the Sumo Logic Cloud SIEM.
PowerShell Protect is a configurable solution for auditing and blocking PowerShell scripts. It integrates with the anti-malware scan interface in Windows 10 and Windows Server 2016 and above. This means that any scripts run within the PowerShell engine will be analyzed with the PowerShell Protect engine.
PowerShell Protect works with Windows PowerShell and PowerShell 7. Additionally, any process hosting the PowerShell Engine, like PowerShell Universal, will also be analyzed by the PowerShell Protect engine.
Sumo Logic Cloud SIEM is a platform for absorbing and analyzing large amounts of log data. You can use their cross-platform agent to consume local logs or ship logs over HTTP. Once within the SIEM, you can parse, analyze and visualize log data. Additionally, you can alert on events and take action when necessary.
PowerShell Protect is distributed as a PowerShell module. You can install the module from the PowerShell Gallery.
Install-Module PowerShellProtect
The engine and AMSI provider are included in the module. Once the module is installed, you will need to install the AMSI provider. You will need to open an administrative PowerShell prompt to do so as it needs to register with the Windows system.
Install-PowerShellProtect
Once the AMSI provider is installed, it will begin analyzing scripts and commands run in terminals. There are numerous built-in rules that will trigger automatically. These built-in rules will block execution of suspicious code that typically results in exploits.
PowerShell Protect is also very configurable. You can use the rule engine to define conditions and take actions such as log to a file or block the execution of a command outright. In order to audit PowerShell scripts for use with Sumo Logic, we’ll define a simple condition and, when the condition is met, store some information to a log file.
PowerShell Protect provides cmdlets for configuring the system. The below example searches for the string webrequest within the commands. You can mix and match conditions and evaluate numerous properties.
$Condition = New-PSPCondition -Property "command" -Contains -Value "webrequest"
Once a condition is met, you can take an action. Actions include blocking the execution of the script, logging the script to a file or sending a log over HTTP. In this example, we’ll log to a file. There are numerous formatting options you can use when taking audit actions. In this case, we’ll create a CSV log file that contains the timestamp, application name and rule name.
You can also include information such as user, domain and script contents.
$FileAction = New-PSPAction -File -Format "{timestamp},{applicationName},{rule}" -Path "C:\logs\powershell.log" -Name 'File'
To cause a condition to trigger an action, you will need to create a rule. A rule can be triggered by one or more conditions and trigger one or more actions. In this case, the Web Request rule will trigger when webrequest is found within the script and issue the File action to log the event to a file.
$Rule = New-PSPRule -Name "Web Request" -Condition $Condition -Action @($FileAction)
The next step is to store the rules within a configuration. The New-PSPConfiguration cmdlet can be used to generate this configuration object.
$Configuration = New-PSPConfiguration -Rule $Rule -Action $FileAction
Once a configuration has been created, you can store the configuration on the system for the PowerShell Protect engine to utilize. As soon as it has been stored, the AMSI provider will start using the configuration. You can store the configuration within the file system or within the registry.
Set-PSPConfiguration -Configuration $Configuration -FileSystem
You’ll notice that when you issue commands such as Invoke-WebRequest in any PowerShell terminal, the log file will be updated. Time stamps are in UTC.
12/1/2021 1:54:12 AM,PowerShell_C:\Program Files\PowerShell\7\pwsh.exe_7.2.0 SHA: bec5c36d9da67bfcf5b88834f03b326c89f100c5,Web Request
12/1/2021 1:54:13 AM,PowerShell_C:\Program Files\PowerShell\7\pwsh.exe_7.2.0 SHA: bec5c36d9da67bfcf5b88834f03b326c89f100c5,Web Request
12/1/2021 1:54:14 AM,PowerShell_C:\Program Files\PowerShell\7\pwsh.exe_7.2.0 SHA: bec5c36d9da67bfcf5b88834f03b326c89f100c5,Web Request
12/1/2021 2:01:39 AM,PowerShell_C:\Program Files\PowerShell\7\pwsh.exe_7.2.0 SHA: bec5c36d9da67bfcf5b88834f03b326c89f100c5,Web Request
12/1/2021 2:53:52 AM,PowerShell_C:\Program Files\PowerShell\7\pwsh.exe_7.2.0 SHA: bec5c36d9da67bfcf5b88834f03b326c89f100c5,Web Request
Now that we have a log file being generated, we can ingest that with Sumo Logic to visualize and report on it.
Create a Sumo Logic account. They offer a 30 day trial if you want to try it out.
First, you’ll need to create a new app within their platform.
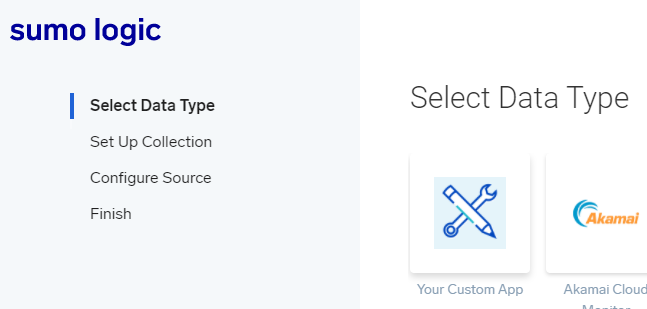
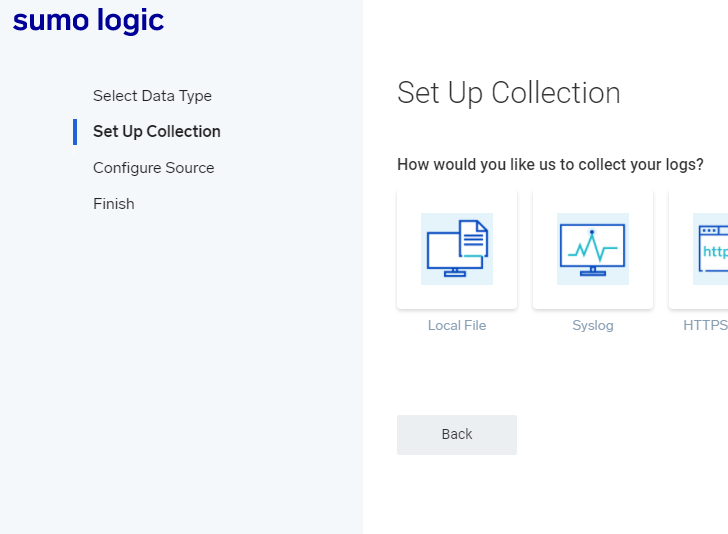
We’ll setup a local file collection. We can monitor hosts for file paths and ship those logs to Sumo Logic using a collector agent.
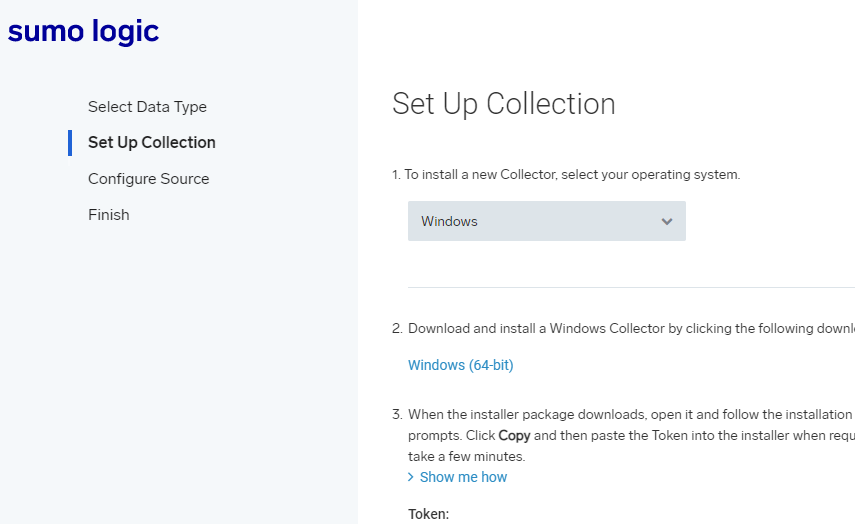
You’ll need to select your platform (Windows in this case), download and install the agent. A token will be provided that you will need to input during installation.
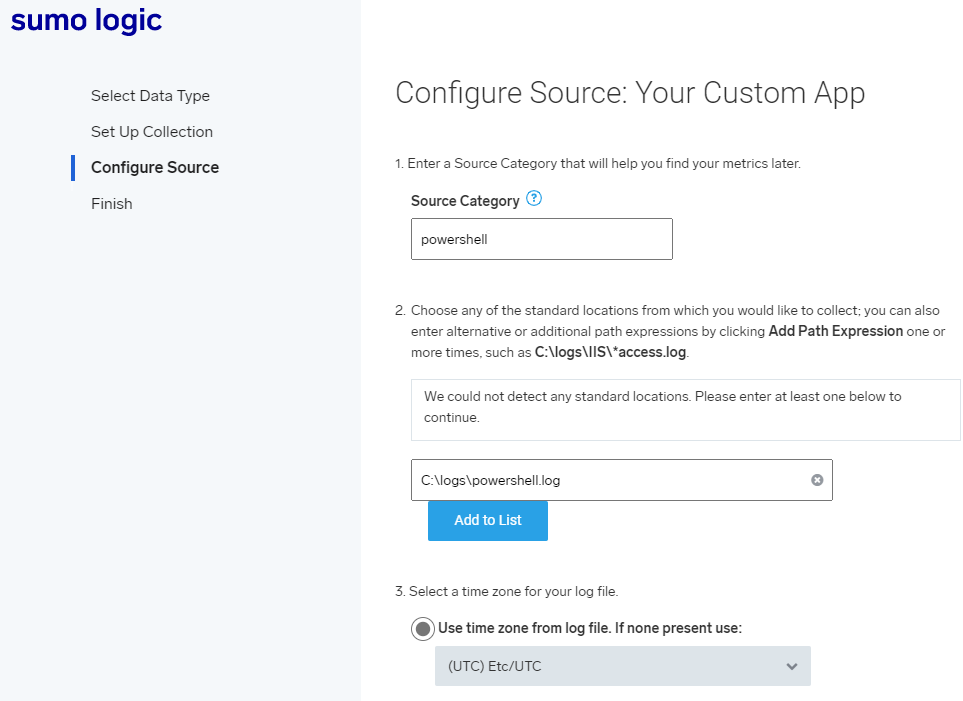
Once you’ve installed and configured the agent, you can configure the collection source. You’ll want the source to match the path of your PowerShell Protect log file. The Sumo Logic agent will monitor for changes to the file and ship them to the Cloud SIEM.
After configuring the source, Sumo Logic will communicate with the agent and begin consuming the logs.
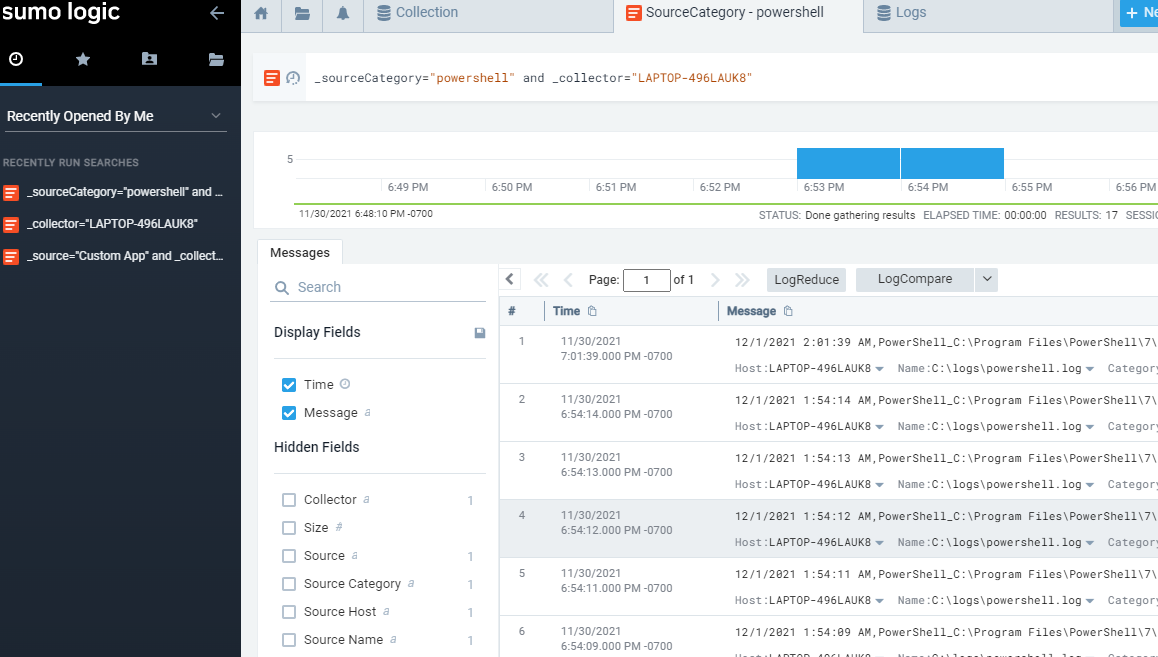
Now that you’ve configured Sumo Logic, you can start to dig into the logs. You can setup parsing rules, time stamp information and charts based on the data consumer from PowerShell Protect.
PowerShell Protect providers low-level, configurable access to audit information about scripts running on your Windows systems. By integrating with Sumo Logic, you can make actionable decisions on data provided by hosts across your system.
Find this useful? Please consider sharing this article. Have a question about PowerShell? Contact us and we'll write a post about it.
Continue the conversion on the Ironman Software forums. Chat with over 1000 users about PowerShell, PowerShell Universal, and PowerShell Pro Tools.
Receive once-a-month updates about Ironman Software. You'll learn about our product updates and blogs related to PowerShell.